Broadly our services in IT Assurance & Compliance consist of:
- a) Business Continuity Planning
- b) Computer Crime Investigations
- c) Training in Information Technology
- d) Compliance with IS policies and procedures

Broadly our services in IT Assurance & Compliance consist of:
a) Business Continuity Planning :- It is the process a company undergoes to create a prevention and recovery system from potential threats such as natural disasters or cyber-attacks. BCP is designed to protect personnel and assets and make sure they can function quickly when disaster strikes. It involves the following procedure:
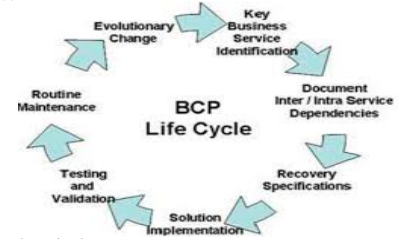
b) Computer Crime Investigations :- This involves audit of any crimes committed, likely to be committed or can be committed by anyone having access to the computer systems of the Company. It ranges from recovering file systems on computers that have been hacked or damaged test security systems that are currently in place this can be done by trying various ways to hack into the corporation’s computer networks. At corporations, computer crime investigators also maximize optimal computer system performance levels.
Computer Crime Investigation involves:
c) Training in Information Technology
d) Compliance with IS policies and procedures